You know what people really like? Government regulation!
...crickets...
Ok, maybe not so much, but this one is actually really important. The General Data Protection Regulation is an EU reg that kicks in on 25 May 2018 so we've got bang on a year to get organised. It's important within the EU because it relates to how data of their citizens and residents is handled and it's important outside the EU because the regulation can impact non-EU organisations too.
I've been interested in GDPR for some time on a couple of fronts. For one, I like the idea of a regulation having some serious teeth when it comes to issuing penalties. This means up to €20M or 4% of annual gross worldwide revenue, whichever is higher. In other words, if you screw up your security bad enough and fail to protect customer data, you may face a fine that really stings. As much as I want to incentivise organisations to do the right thing, there needs to be a stick for those who just don't get it.
I was also particularly interested in how the regulation impacts the handling of personal data. This is a really central component of the regulation and GDPR covers everything from how you acquire it to how you store it and then eventually, how you dispose of it (yeah - stop keeping data forever just because storage is cheap). For example, it requires consent from the "data subject" (the person whose data we're talking about) and that consent must be freely given, specific, informed and unambiguous. In other words, no sneakily grabbing their data and using it in ways they wouldn't expect. There's a lot more to it than that, of course, but the main theme that runs throughout GDPR though is giving people back control of their data.
Recently, Varonis asked me if I'd be interested in writing a course for them which they could then make freely available to the public. This is actually the fifth one of this nature I've done for them after The Top Web Security Risks, Introduction to Ransomware, Insider Threats and Internet Security Basics . I'm very happy to see this one now live and freely available, particularity given I'm about to head to Europe for 6 weeks where this is obviously a big topic!
But while I'm here, let me cover off something that has been raised with me many times in the past and until now, I didn't feel sufficiently informed to comment on: the impact of GDPR on Have I been pwned (HIBP). The question I was regularly asked amounted to "how will you run HIBP when there's a lot of EU folks' data in there"? Let me answer this in two ways, firstly by talking about the mechanics of HIBP:
As of today, there's going on 3.8 billion records of data in the system. A breach happens, I extract the email addresses, load them in and it's job done. I have no idea how much of the data is from where in terms of countries of origin. Sometimes, I could work it out by looking at the attributes of a record which contain, say, a person's physical address. But very frequently that's not present and the two massive combo lists I loaded earlier this month are evidence of that (they only had email address and password). I could make assumptions about addresses on domains with Euro TLDs (anything .nl would be Dutch), but that would neglect the significant number of Europeans using gmail.com or similar addresses. In short, I have absolutely no way of consistently and reliably identifying Europeans in the data. But even if I did, does that then mean I should exclude them from the ability to use this service? Now there's a bigger issue around the responsibility of running it any making any data publicly searchable (and incidentally, I have a post in draft about that), but you can see the challenge.
But here's the aspect of GDPR that I think is particularly interesting and it relates to this whole extraterritoriality thing, that is how it applies outside of the EU. Drawing directly from the published regulation, here's what GDPR says about handling EU folks' data outside of the EU:
the processing of personal data of data subjects who are in the Union by a controller or a processor not established in the Union should be subject to this Regulation where the processing activities are related to offering goods or services to such data subjects irrespective of whether connected to a payment
For those entirely unfamiliar with GDPR, the controller is the organisation that collects data from the data subjects (normal people like you and I), whilst the processor can be the likes of a cloud provider on which the service in question runs (I define all of these in a dedicated module within the course). Reading this, you can see how some people might jump to the conclusion of "all systems holding EU data are subject to GDPR", but it's important to read further. What's key here is whether you "envisage offering services to data subjects in one or more Member States in the Union" or in other words, are you specifically targeting Europeans. GDPR then goes on to define a number of factors which can indicate this, including:
the use of a language or a currency generally used in one or more Member States with the possibility of ordering goods and services in that other language, or the mentioning of customers or users who are in the Union, may make it apparent that the controller envisages offering goods or services to data subjects in the Union
It goes beyond just that one snippet, but you get the idea. In the course, I talk about the following 4 factors which regularly appear within GDPR documentation:

If you were to see any of these on a website, you could reasonably conclude that there's a good chance it's targeting folks in the EU. Let's pick a real-world example - the Hong Kong based Strawberrynet. Now admittedly, I have a history with these guys and I most recently wrote about them in the Hold my beer blog post where I showed outrageously bad privacy practices. Here's a site that allows you to enter an email address - any email address - and it will come back and give you the owner's name, address and phone number. No, it's not a flaw, it's literally by design! It's about as anti-GDPR as you can get because it demonstrates a total disregard for the "data subject's" personal data.
Let's take a look at Strawberrynet after connecting to them from the Netherlands:
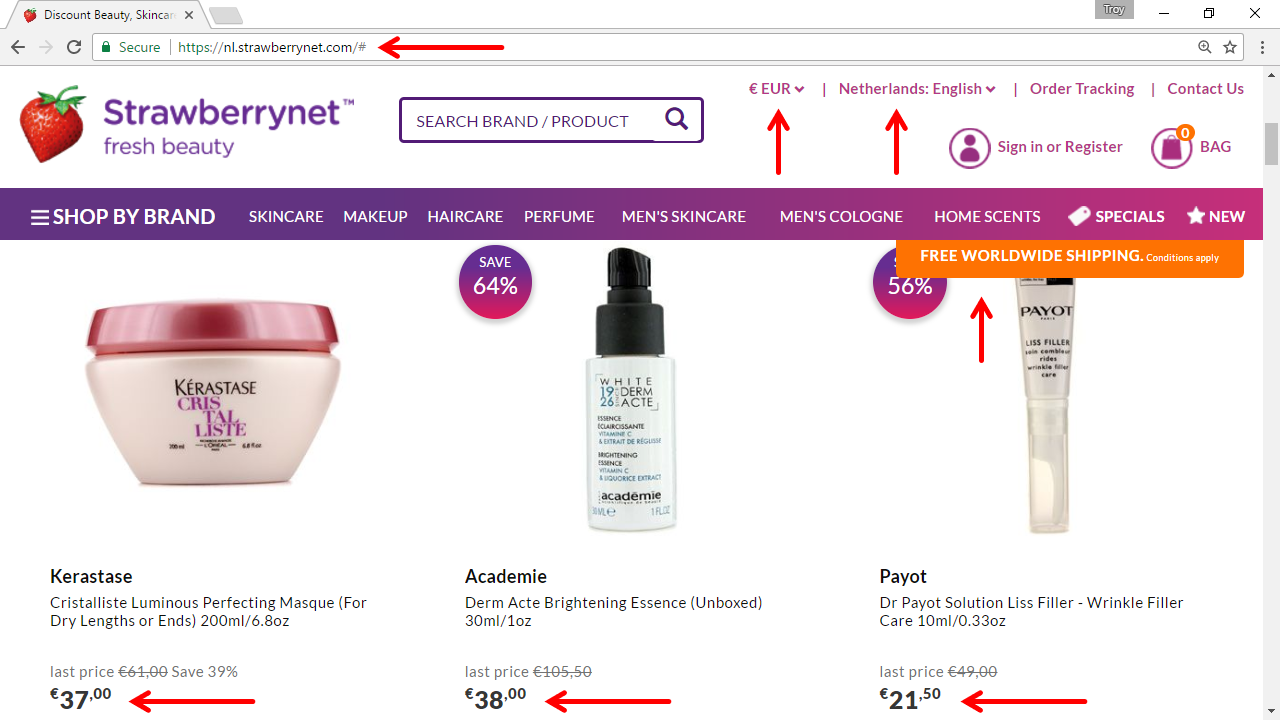
When you consider the areas of the site I've highlighted here, would you reasonably conclude that Strawberrynet is envisaging "offering services to data subjects in one or more Member States in the Union"? Without a doubt. This is precisely the sort of site that will come under the scope of GDPR extraterritoriality and if they keep this up, we may well get to see just how effective that component of GDPR is.
But let's take an example at the other end of the spectrum - my cat forum. Hypothetical of course, but imagine I stand up a site like this:
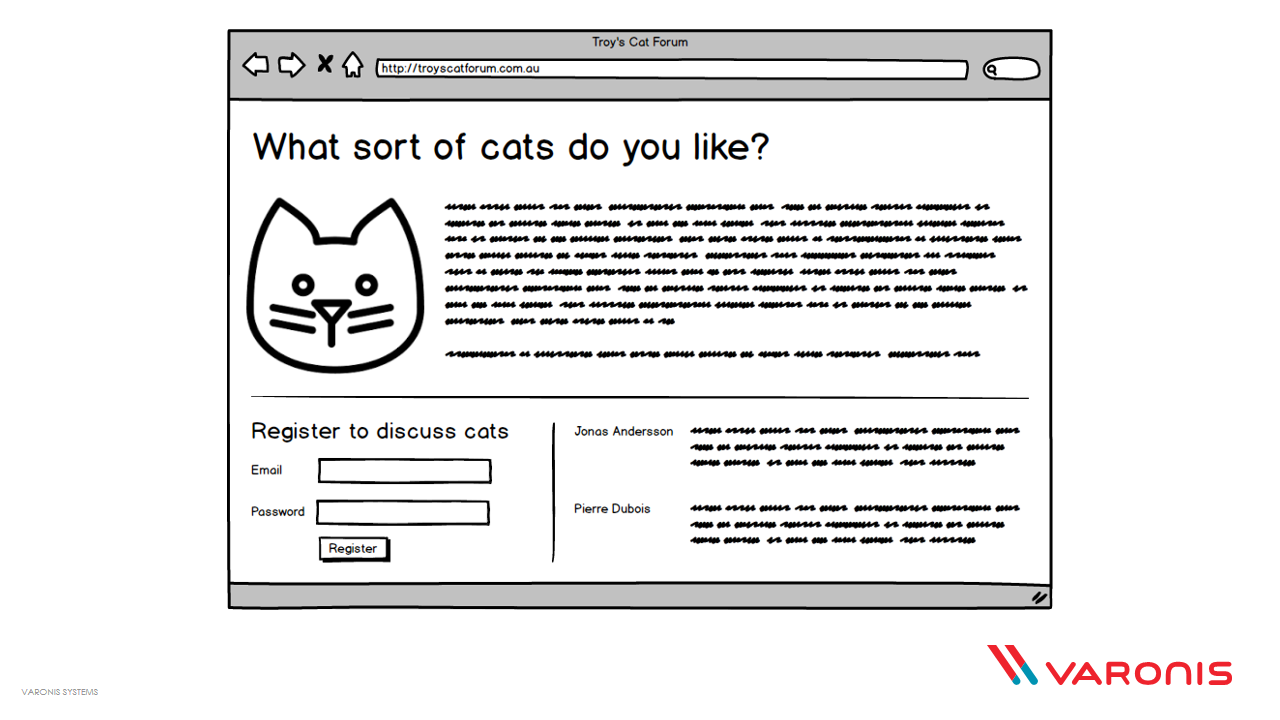
It talks about cats. You can register and comment on cats. There are very European names there discussing cats and people from the EU are able to do this because that's the nature of the internet - it's global. But being globally accessible doesn't put a cat forum under the scope of GDPR. It's not specifically marketing to EU folks, it's not providing goods in their currencies and for all intents and purposes, it's a global service with no favouritism or targeting to any one part of the world. It's just a cat forum.
And that's where HIBP sits too - it's merely a site on the internet. There's a lot of European data in there simply by virtue of Europe being on the internet, not because I'm specifically curating a European audience.
One thing that many of the people I spoke to while creating this course agree on is that there are many aspects of GDPR we need to wait to see tested before knowing how strictly they'll be applied. That whole "up to 4% of gross annual revenue" thing, for example, really has some teeth but we don't know how liberally the penalty will be levied yet. There also remains a lot of grey area and as the countdown to May 25 next year continues, there's increasing awareness within many organisations and as a result, plenty of people are lining up to feast on the opportunity that presents:
Writing a course on GDPR. Is it just me, or are a lot of lawyers making a lot of money out of this?
— Troy Hunt (@troyhunt) May 1, 2017
It's an interesting time and both the lead-up to May 25 next year and the ensuing months and years as it settles in will be telling. For now though, the GDPR Attack Plan is now live and freely available - enjoy!